Thursday, 31 March 2016
CIO interview: Retail’s past a poor guide to future, says Paul Coby of John Lewis
Paul Coby, IT director at John Lewis, believes retailers will need to move with changing customer patterns and demands to survive the omni-channel shift
How to transition to a cloud-based analytics environment
Accenture Digital consultants say businesses can be more agile by way of cloud-based analytics
FBI to apply iPhone security bypass in second case
The FBI is to help unlock an iPhone in an Arkansas murder case, deepening fears that the method used to break into the San Bernardino gunman’s phone will be applied more widely
Businesses should help shape graduates, says Hitachi Data Systems COO
Lynn Collier, COO of Hitachi Data Systems, wants businesses to collaborate with educational institutions to ensure young people gain the right skills
Adwind at centre of cyber attack on Singapore bank
Kaspersky Lab has revealed that the Adwind malware-as-a-service platform was at the centre of an attack on a Singapore bank
Build out networks and mobile to rebalance UK economy, says O2
In a major report, mobile operator O2 suggests that access to better digital infrastructure could boost the UK economy by £1.5bn outside of London and the South East
DDoS attacks on universities normally performed by “disgruntled” students or employees
The majority of distributed denial of service attacks on universities are made by students or employees, says the head of infrastructure services at the University of London
MedStar says it is recovering from suspected ransomware attack
US hospital group MedStar says it is restoring its IT systems after reportedly being hit by a stealthy new strain of server-targeted ransomware
New London mayor urged to take ‘drastic action’ on capital broadband
A YouGov poll for the Foundation for Information Society Policy finds widespread disillusionment among Londoners when it comes to broadband provision in the capital
Fintech axe to fall on a third of banking jobs over next 10 years
More than a third of jobs at European banks will disappear over the next decade as the adoption of fintech-based services grows
Teardown of Oculus Rift finds good design that’s somehow relatively easy to repair
 When a new category of gadget appears, it’s understandable when the vanguard devices aren’t the most well designed, or are resistant to disassembly and repair. Fortunately, that doesn’t seem to be the case with the first headset from Oculus, iFixit has found. Read More
When a new category of gadget appears, it’s understandable when the vanguard devices aren’t the most well designed, or are resistant to disassembly and repair. Fortunately, that doesn’t seem to be the case with the first headset from Oculus, iFixit has found. Read MoreWednesday, 30 March 2016
Cyber criminals use Microsoft PowerShell in ransomware attacks
A newly discovered family of ransomware, dubbed PowerWare, uses Microsoft PowerShell to target organisations through macro-enabled documents
San Francisco data analytics early-stage firms point to third-wave BI
California start-up and early-stage data analytics companies are positing technologies that point beyond second-generation business intelligence, such as Qlik and Tableau
Security researchers warn of server-attacking ransomware
New strain of ransomware said to be distributed by compromising servers and using them to move through networks to encrypt and hold multiple data sets to ransom
British-Swedish research team breaks spectrum efficiency record
Engineers at the University of Bristol and the University of Lund show how a multiple antenna system can offer a 12-fold increase in mobile spectrum efficiency
What is behind the slowdown in public-sector sales of ‘true cloud’ services via G-Cloud?
With sales of “true cloud” services via G-Cloud showing signs of slowing down, Computer Weekly asks the experts the reasons why
Security should be driven by business, says Corvid’s Andrew Nanson
Information security should be business-driven and investments assessed for their effectiveness and business value, according to Corvid CTO
EE still generating most broadband complaints, but volumes fall
The overall volume of complaints about broadband services dropped during the last three months of 2015, says Ofcom
Centrica deploys large scale Hortonworks cluster to boost business
Utility company Centrica is looking at how to grow the business by harvesting data lakes
CW@50: Fertile British breeding grounds for information security innovation
Computer Weekly is marking its 50th anniversary this year with a series of articles celebrating 50 years of British technology innovation. In this article, we look at the evolution of information security threats and some of the British innovation to counter those threats
Hackers to probe engine control units amid emissions scandal
ICCT hires computer whizz-kids to find out who else besides Volkswagen uses ‘defeat devices’ in cars
Zerto adds file level recovery to Virtual Replication
Cross-hypervisor, storage-agnostic Zerto Virtual Replication version 4.5 allows customers to recover files to any point in time, such as prior to deletion, virus or corruption
Razer takes aim at game streaming community with Ripsaw capture card
 Razer’s Ripsaw is far from the first game capture card, but it leapfrogs the competition nicely and takes aim at a growing population of streamers who are willing to pay good money for an easily set up solution with industrial-strength capabilities. Read More
Razer’s Ripsaw is far from the first game capture card, but it leapfrogs the competition nicely and takes aim at a growing population of streamers who are willing to pay good money for an easily set up solution with industrial-strength capabilities. Read MoreTuesday, 29 March 2016
The dawn of managed services in the Middle East
Managed services are on the up in the Middle East, with enterprises looking at ways to support critical infrastructures while they invest in new technologies
St Andrews University uses IoT to monitor seal populations
The Sea Mammal Research Unit at the University of St Andrews is connecting harbour seals to the internet of things to try to learn why their populations are declining
Sweden’s central bank puts brake on cash-free society
Sweden has been on a fast track to become the world’s first cashless society, but now its central bank is stamping on the brakes
Hunters: a rare but essential breed of enterprise cyber defenders
They wait, they watch, they search the outer reaches of networks and the darkest corners of the web, setting traps, crafting tools, collecting evidence and going in pursuit: they are the hunters
OSNexus unlocks Ceph object storage in QuantaStor v4
Software-defined storage maker OSNexus adds Ceph-based object storage to its QuantaStor product, adding it to block and file storage from ZFS, Gluster and Ceph
University of Reading deploys IPv6 on Malaysian campus
The University of Reading has recently built a campus in Malaysia, allowing a new network design deploying IPv6 from the outset
Why are telcos so readily adopting open standards for NFV?
Communications services providers are lining up to make their future virtualised networks as open as possible. What’s the attraction?
DNB to close 59 branches in Norway as online banking dominates
Norwegian bank DNB is closing branches and cutting jobs as more customers move to digital channels
Apple vows to raise security as FBI breaks into iPhone
Apple says it will help law enforcement with investigations, but will increase the security of its products after the FBI broke into an iPhone
Thailand to strengthen broadband backbone
Thailand's government is investing heavily in communications infrastructure to make the country’s broadband fit for the digital age
FBI investigating cyber attack on US hospital group Medstar
US hospital group Medstar Health appears to be the latest target of ransomware as it suspends IT system to halt malware infection
Fibre altnet B4RN may get code powers to build out network
Ofcom has started a consultation to give community-backed fibre-to-the-premises altnet B4RN new powers to roll out its network on a wider scale
Nintendo’s first smartphone app, Miitomo, arrives in the U.S. and other markets this Thursday
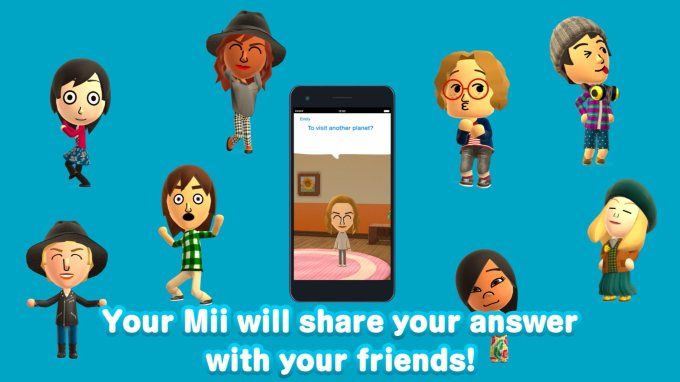 Nintendo’s first smartphone application, “Miitomo,” now has a U.S. launch date: March 31st. In addition, the company says it will also be available in several other countries at the same time. While the company didn’t detail which countries will also receive the app, it will likely include several European markets, and others available on the list posted here to the… Read More
Nintendo’s first smartphone application, “Miitomo,” now has a U.S. launch date: March 31st. In addition, the company says it will also be available in several other countries at the same time. While the company didn’t detail which countries will also receive the app, it will likely include several European markets, and others available on the list posted here to the… Read More5 hard questions facing Oculus Rift
 Today, the future became the present with the launch of the Oculus Rift. The reviews are in, but uncertainty hangs overhead with HTC and PlayStation’s VR headsets still on the way.
Here are the tough questions that will determine what you should buy, the distribution of power between the platforms, and VR’s effect on our lives.
Should people buy Oculus Rift consumer v1, or wait… Read More
Today, the future became the present with the launch of the Oculus Rift. The reviews are in, but uncertainty hangs overhead with HTC and PlayStation’s VR headsets still on the way.
Here are the tough questions that will determine what you should buy, the distribution of power between the platforms, and VR’s effect on our lives.
Should people buy Oculus Rift consumer v1, or wait… Read MoreSunday, 27 March 2016
Brussels attacks prompt renewed EU focus on airline passenger data
The controversial plans to collect passenger name records for airline travellers in the EU are under focus after the terrorist atrocities in Brussels
Urban broadband speeds three times higher than rural
Ofcom releases statistics on average broadband speeds in the UK and finds the gap in experience between town and country dwellers remains as wide as ever
Government warned of smart meter security threat back in 2012
The government was warned four years ago that its plans for a nationwide smart meter roll-out represented a “potentially significant” security and privacy threat, Computer Weekly has learned
BT says geography biggest barrier to finding apprentices
Telecoms provider BT says that skilled young people for apprenticeships are readily available, but that it struggles to find them outside of London
KPMG accelerates transfer of UK IT jobs to India
KPMG is moving more jobs to India, with UK contractor roles the most affected
Santander launches voice-controlled banking
Santander has made technology available that enables its customers to control its mobile banking app and access information using their voices
T-Systems targets Amazon cloud customers
Deutsche Telekom's IT services division plans to take business from Amazon with a cheaper public cloud that guarantees users' data stays in Germany
Friday, 25 March 2016
Tech firms urge further improvements to snoopers’ charter
Major US tech firms have told the UK’s Investigatory Powers Public Bill Committee that their main concerns have yet to be addressed, and have urged further amendments
BMW Group signs HPC and hosting deal with hydro-powered Swedish datacentre operator
BMW Group inks deal with green datacentre operator in Sweden
Retro gaming fans rejoice: Atari Vault is on Steam with 100 games
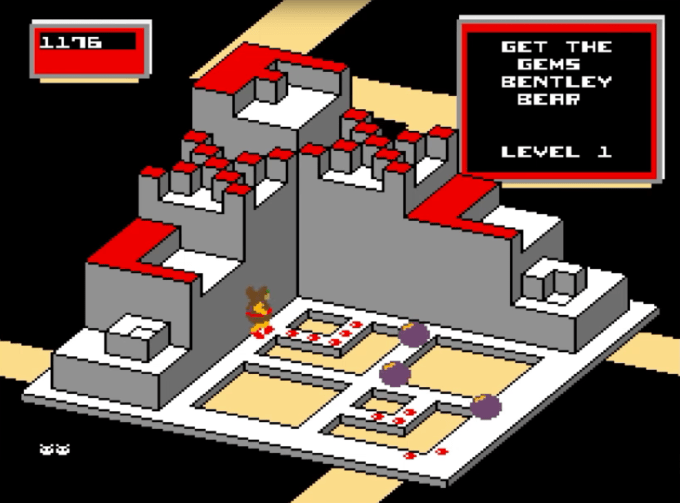 Longing for the days of the sticky floored arcades of your youth and long nights spent with the the Atari 2600, but can’t be bothered to dig through your mum’s basement to find all the bits and bobs to throw yourself into a retro-gaming binge? Aren’t you in some industrial-strength luck. Available starting today on Steam, Atari Vault gives you 100 retro games to while away… Read More
Longing for the days of the sticky floored arcades of your youth and long nights spent with the the Atari 2600, but can’t be bothered to dig through your mum’s basement to find all the bits and bobs to throw yourself into a retro-gaming binge? Aren’t you in some industrial-strength luck. Available starting today on Steam, Atari Vault gives you 100 retro games to while away… Read MorePhishing attack at US retailer underlines need for proactive security
Security experts say a phishing attack on US retailer Sprouts Farmers Market shows the need to educate employees and correctly configure IT systems
Metcalfe’s law of connections will drive digital business value
Robert Metcalfe, the co-inventor of Ethernet, proposed that the value of network cards increases as the number of networked devices grows
Businesses urged to update Apple software to dodge zero-day attacks
Security experts are urging Apple Mac, iPhone and iPad users to update their operating systems to avoid data-stealing attacks that exploit a new zero-day vulnerability
CIO interview: Martin Uudelepp, Fonus Group
The interim CIO of Swedish family law and funeral group Fonus tells Computer Weekly about his role as a “chaos pilot”
Cloud, compliance and data protection top storage priorities for 2016
The results are in for Computer Weekly’s IT priorities survey 2016, with storage and backup for virtual servers a key task while flash storage has plateaued
Thursday, 24 March 2016
US hospital claims to have fought off a ransomware attack
A hospital in Kentucky claims to have regained control of its IT systems five days after cyber criminals hit it with a ransomware attack
Ofcom makes it easier for users to switch mobile networks
Telecoms regulator Ofcom launches a consultation on how to make the process of switching mobile network easier for consumers
Canadian Elizabeth Denham set for the UK's next information commissioner
Canadian privacy commissioner Elizabeth Denham is to become the UK's next information commissioner as government pushes ahead with the snoopers' charter
UK tech industry welcomes government’s new anti-crime strategy
Only a modern strategy that incorporates technological advances and the greater use of data analytics can improve UK crime prevention, says TechUK
Government launches consultation on 10Mbps broadband obligation
DCMS begins the consultation process to implement a nationwide universal service obligation for broadband of 10Mbps
GDS preps guidance for third-party suppliers to deliver 'government as a platform'
Government Digital Service (GDS) chief insists "pragmatic extensions" to outsourcing contracts implies nothing permanent in push for "government as a platform" (GaaP)
Danish utility NRGi goes offshore for IT platform transformation
Danish utilty NRGi has outsourced its IT to Indian services supplier Wipro as it attempts to transform its operations amid increased competition
Internet of things developers to get new spectrum licences
Ofcom will launch a new licence product to more adequately address and accommodate IoT use cases later in 2016
Google ups ante in cloud infrastructure services with global datacentre expansion plans
Google is set to expand global datacentre footprint, as competition in the cloud infrastructure services market heats up
Chinese man admits conspiring to hack US military secrets
A Chinese national working in Canada has pleaded guilty to helping hackers in China access US military secrets from defence contractors, including fighter jet blueprints
Welsh secretary calls for taller mobile masts
The Welsh secretary Alun Cairns has called on the devolved government to consider allowing mobile operators to build taller masts
Famous dodges Apple iTunes ban with web app
 The Famous app got itself banned from Apple’s App Store about a month ago. They sidestepped the ban by promptly launching an Android version instead, and is today back on an iOS device near you in the form of a web app. For the new version, the company recycled much of the game mechanics, minus the commenting and chat functionality that made it prime bullying real estate. Read More
The Famous app got itself banned from Apple’s App Store about a month ago. They sidestepped the ban by promptly launching an Android version instead, and is today back on an iOS device near you in the form of a web app. For the new version, the company recycled much of the game mechanics, minus the commenting and chat functionality that made it prime bullying real estate. Read MoreSony announces plans to make PlayStation games for iOS and Android
 It looks like Sony will follow Nintendo’s cue and focus on mobile gaming. The company announced today [in Japanese] that it has formed a new business unit that will bring PlayStation titles and IP to iOS and Android devices. Read More
It looks like Sony will follow Nintendo’s cue and focus on mobile gaming. The company announced today [in Japanese] that it has formed a new business unit that will bring PlayStation titles and IP to iOS and Android devices. Read MoreRazer goes budget-friendly with new Blackwidow X keyboard line
 In the world of gaming accessories, “budget-friendly” is not a word frequently used. Naturally, one of the biggest players industry, Razer, aims to change that with the Blackwidow X. The newest set of keyboards added to their existing lineup, the Blackwidow X has changes made not only to improve simplicity, but to promote more competitive (e.g. budget-friendly) pricing for… Read More
In the world of gaming accessories, “budget-friendly” is not a word frequently used. Naturally, one of the biggest players industry, Razer, aims to change that with the Blackwidow X. The newest set of keyboards added to their existing lineup, the Blackwidow X has changes made not only to improve simplicity, but to promote more competitive (e.g. budget-friendly) pricing for… Read MoreTuesday, 22 March 2016
Only 42% of infosec pros use threat intelligence, survey shows
Cyber threat intelligence sharing is a necessity, says Intel's McAfee Labs – but less than half of infosec pros use it, despite the benefits, a survey reveals
Cyber security budgets not rising in line with threats, say security pros
While it is good news that businesses are increasing investment, it is clear that spending on security is still not at a level that matches the changing threat landscape, says IISP
How Orange France engaged influencers to launch its IoT service
Orange France engaged influencer marketing specialist Traackr to successfully launch its Homelive internet of things (IoT) service
CW@50: From Captain Kirk to 5G – 50 years of mobile
As Computer Weekly prepares to celebrate the 50th anniversary of our first edition in 1966, we look back at 50 years of British innovation and development in mobile networking
Ofcom forces BT Openreach to cut wholesale leased line prices
Ofcom forces BT Openreach to cut its wholesale prices for leased lines and imposes stricter services standards
Investigatory Powers Bill: What it means for UK tech startups
The proposed Investigatory Powers Bill could prove damaging for innovative high-tech companies, writes Tirath Bansal, founder and CEO of internet startup myorb.com
Intel's former chief Andy Grove dies, aged 79
Andy Grove, Intel’s former chairman who helped the company make the change from memory chips to processors, passes away at the age of 79
Monday, 21 March 2016
CW500: Peter Connor from Home Retail Group on digital transformation
We look at the people, process and cultural challenges for your business brought about by digital transformation
CW500: Chris Boyd from Telefonica on digital transformation
We look at the people, process and cultural challenges for your business brought about by digital transformation
South Dublin County Council declares Amazon datacentre planning application "invalid"
Amazon appears to have fallen foul of Irish council’s planning regulations, potentially delaying its latest datacentre building project
National Cyber Security Centre to be UK authority on information security
The UK’s National Cyber Security Centre (NCSC) is to be the UK's one-stop authority on infosec, based in London and led by GCHQ's Ciaran Martin
Southend Council to connect key sites with dark fibre network
Southend-on-Sea Borough Council selects CityFibre to supply a 50km dark fibre network across 120 public sector sites in the town
Juggling a diverse user infrastructure
CISOs are facing an increasingly fluid workplace and control of modern IT systems needs to reflect this dynamism
Gigaclear hits 10,000 Oxfordshire properties with ultrafast broadband
Home FTTP broadband network builder Gigaclear’s commercial roll-out in Oxforshire approaches a major milestone with the connection of its 10,000th property
Britain to pay billions for monster internet surveillance network
New questions raised about Britain’s snoopers charter after Denmark abandons its own UK-style surveillance programme for a second time
Sunday, 20 March 2016
Germany-Finland subsea cable tipped to fuel European datacentre market growth
The deployment of a European subsea data cable could put Finland on the map for datacentre investors
Internet of things needs more innovative business models
At a government event on IoT policy, speakers call for more innovative business models and joined up thinking to enable the IoT to live up to its potential
Nationwide unifies business and public Wi-Fi in 700 branches
Nationwide Building Society rolls out a unified Wi-Fi network across both its public and enterprise properties
Leaked documents foretold problems with Australia's national broadband strategy
External and internal documents suggest Australia's national broadband network (NBN) roll-out is likely to waste A$29bn
Computer Weekly at 50: Celebrating 50 years of British technology innovation
To celebrate the forthcoming 50th anniversary of the first issue of Computer Weekly, we launch a major editorial programme on British IT history
New UK law will criminalise failure to hack on demand
MPs have been given only two weeks to read 1200 pages of documents which disclose new powers to require technology companies to install secret surveillance capabilities in software, computer equipment or networks.
Saturday, 19 March 2016
UK workers more diligent about cyber security at home
UK employees expect an IT safety net to protect them at work and are more willing to take responsibility for security at home, a survey commissioned by Citrix has revealed
Australian girls believe online harassment is endemic
There are clear signals that online threats against women and attempts to invade their privacy are becoming societal norms in Australia
Eurocrats clash over EU-US Privacy Shield data protection deal
There remains significant disagreement in Brussels over the EU-US Privacy Shield arrangement intended to replace Safe Harbour
Cyber crime is driving UK fraud losses, totalling £755m in 2015
Payment card fraud accounted for 75% of UK fraud losses in 2015, most of which was remote purchase fraud using card details stolen though data hacks and malware, says FFA UK
What does the IT sector think of the UK potentially leaving the EU?
The referendum on the UK’s membership of the European Union is fast approaching and the country’s IT sector is taking sides
UK outsourcing sector wants to remain in a reformed EU
A survey of UK outsourcing companies reveals that three quarters of all respondents want to remain in a reformed European Union (EU)
Friday, 18 March 2016
Danish taxi drivers protest against Uber at startup event
Taxi drivers in Denmark protest about the inclusion of Uber at Nordic Startup Conference in Copenhagen
FBI issues warning about car hacking
US security service calls on consumers and vehicle manufacturers to take steps to reduce the increasing risk of car hacking and to report incidents
Most students say cyber security is a growing threat
Some 70% of higher education students say they are aware that cyber crime and attacks are a threat, but less than half think security is their responsibility
TechUK calls for closer ties between cloud and communications providers
Technology association TechUK outlines measures to encourage greater adoption of cloud computing in the UK - starting with greater connectivity
CIO interview: Mogens Kristensen, Sydbank
Danish bank’s IT head explains the advantages of sharing some IT systems with other banks
Everyone should be a chief customer officer, says PetsPyjamas CEO
CEO of pet-friendly product company PetsPyjamas says the idea of the chief customer officer is redundant
CIO interview: Charlotta Nyström, Kemira
Finnish chemical industry group CIO sees networking with other CIOs as an essential part of her job
Dropbox invests in building out on-premise storage as user numbers soar
Cloud-based file share and sync service reveals details of its hybrid cloud strategy, which has seen it invest large sums in building its own on-premise infrastructure
Growing need for IT training in the Middle East needs careful planning
IT training is becoming increasingly important in the Middle East – but organisations must look beyond suppliers' accreditation schemes
Sophos raises five concerns about snoopers’ charter
As the draft Investigatory Powers Bill takes another step to becoming law, Sophos raises five key concerns that remain even after its revision
Thursday, 17 March 2016
Budget: Osborne pledges £10m for ONS data science hub
Chancellor of the Exchequer George Osborne endorses findings of Charles Bean report on upgrading government statistics and pledges £10m to new data science hub for the Office of National Statistics
Which IT services suppliers are European businesses most satisfied with?
TCS has won top spot for European customer satisfaction for the third year running, according to Whitelane Research
Private mobile network powers Ocado’s robotic warehouse
Online supermarket Ocado rethinks 4G mobile technology to power a network of 1,000 robot workers operating in the grocer's 'hive' warehouse
AWS at 10: How the cloud giant shook up enterprise IT
A decade on from the launch of its first cloud service, the UK managing director of Amazon Web Services reflects on its first 10 years in business
Apple emerges as Google Cloud Platform user – report
Report suggests Apple has joined Spotify in signing up to use Google’s cloud infrastructure services
Cyber security is becoming a Dutch export
IT security is about to rival cheese, tulips, windmills and flood defences as an export from the Netherlands
Most Britons adopting IoT devices cannot secure them
Two-thirds of UK consumers are concerned about the security of IoT devices – but nearly 75% cannot take steps to secure them, a survey reveals
Nintendo’s first smartphone app, a social game called Miitomo, launches in Japan
 As promised last fall, Nintendo has launched its first mobile smartphone application – but it’s not a new Mario game, and the app is for now only available in Japan for the time being. Today, the company unveiled “Miitomo,” a social app that lets users create cartoon-like avatars of themselves – like the “Miis” that Nintendo introduced with the launch… Read More
As promised last fall, Nintendo has launched its first mobile smartphone application – but it’s not a new Mario game, and the app is for now only available in Japan for the time being. Today, the company unveiled “Miitomo,” a social app that lets users create cartoon-like avatars of themselves – like the “Miis” that Nintendo introduced with the launch… Read MoreWednesday, 16 March 2016
Apple iCloud and Gmail hacker set to plead guilty, say US authorities
A US hacker faces up to five years in jail and fines of up to $250,000 after admitting he accessed more than 100 Apple iCloud and Gmail accounts illegally
Salford Council puts gigabit fibre into public housing
Salford Council in Greater Manchester is to deploy fibre to the premises (FTTP) broadband across its council housing portfolio
Crypto ransomware lurks in ads on popular websites
Security researchers warn that the major ransomware malvertising campaign that hit popular websites at the weekend may not be over yet
JD Williams uses analytics to move from mail order to omni-channel
JD Williams’ head of web analytics explains how the firm is using data to provide a personalised experience for customers
Teens interested in tech, but few seek career in engineering
Most teens show an interest in technology, but do not want careers in engineering due to industry misconceptions
Huawei and Samsung trial connected city lighting
Networking suppliers both announce internet of things lighting solutions for smart cities
Atom Bank to offer artificial intelligence-based customer support
Digital bank is integrating AI into its mobile banking app for customers to access support
Rolls-Royce cloud HR project will pay for itself in two years
HR IT director Mark Judd explains how engineering and aerospace firm swapped ageing ERP and spreadsheets for a company-wide core HR system
Fintechs want to take one-third of traditional banks’ business
Banks know they could lose large chunks of business to fintech firms, but if the challengers have their way, it will be more than expected
Budget 2016: Osborne commits to timescale for 5G planning
In a technology-light Budget, chancellor George Osborne made new commitments to future 5G mobile networks
EeGeo picks up $5M to build better 3D visuals for interiors and VR experiences
 Startups working on high-quality immersive visuals and the tech to achieve them are in demand these days, and today one that focuses specifically on interactive outdoor and indoor 3D mapping is announcing a round of funding to help fuel its growth.
London-based eeGeo, which works with the likes of Cisco, Samsung and more on mapping applications for consumers and businesses, has raised $5… Read More
Startups working on high-quality immersive visuals and the tech to achieve them are in demand these days, and today one that focuses specifically on interactive outdoor and indoor 3D mapping is announcing a round of funding to help fuel its growth.
London-based eeGeo, which works with the likes of Cisco, Samsung and more on mapping applications for consumers and businesses, has raised $5… Read MoreCyber security study reveals lack of boardroom governance across UK industries
While 81% of UK boards have increased cyber security scrutiny after the TalkTalk breach, only 53% have data breach management plans in place, a survey has revealed
Retail banking will be fully automated by 2020, say bankers
Financial services employees believe the future of customer retail banking will be automated as the need for digital technology increases
Native OSVR support comes to Unreal game engine
 For gamers worried about exclusive Oculus titles and the diverging future of content support on virtual reality, OSVR is making a bid to take over the platform and ensure that content is available across all hardware. The ecosystem received a major vote of confidence today from one of the largest gaming engines used by developers. Sensics, which helped lead the creation of OSVR alongside… Read More
For gamers worried about exclusive Oculus titles and the diverging future of content support on virtual reality, OSVR is making a bid to take over the platform and ensure that content is available across all hardware. The ecosystem received a major vote of confidence today from one of the largest gaming engines used by developers. Sensics, which helped lead the creation of OSVR alongside… Read MoreTuesday, 15 March 2016
Europe’s CIOs examine impact of new data protection regulation
Belgian IT leader group Beltug is joining other organisations across Europe in preparing for the General Data Protection Regulation (GDPR)
CW@50: 1966 - Computer Weekly goes to bat for the British computer industry
Launched in 1966 as part of a modernising wave to change British society, Computer Weekly battled for the nation’s industry against the US, and saw IT as an entry ticket to the Common Market
Automated financial advice service causes RBS job losses
RBS announces job cuts as it invests in automated services designed to give online financial advice
CW@50: The heyday of British computing - how the Brits ruled IT
We examine how the 1940s, 1950s and 1960s became an age of great innovation for the British computer industry
IT decision makers admit they need to do more to protect data
More than a quarter of IT decision makers at UK organisations admit they need to do more to protect data, a survey reveals
IAM is the future for managing data security
Why is identity and access management is taking centre stage in companies’ access policies
Retailers are in the “dial up” stage of omni-channel
A Retail Business Technology Expo panel likened the current omni-channel movement to the dial-up stage of internet connectivity
Monday, 14 March 2016
Pure aims at unstructured data with Flashblade flash system
Pure Storage charts new waters with all-flash storage array that aims at unstructured and big data analytics workloads with a scale-out modular architecture
Impact of Investigatory Powers Bill is unclear, say most Britons
Open-Xchange privacy survey shows many Britons are unsure and concerned by controversial bill on the eve of of it moving a step closer to becoming law
CIO Interview: Janne Suuriniemi, Finland’s National Police Board
Finland’s National Police Board CIO overhauls a major IT transformation in mid-flight. He tells Computer Weekly about the challenges and his answers to them
IoT “plug and pray” all over again, says security consultant
The increasing interconnectedness of IoT systems and services creates vulnerabilities that are making ‘cascade failure’ almost inevitable, says security consultant David Alexander
UK government and EU Parliament step up big data analytics policy push
UK and EU policy makers are urging governments to raise their data analytics game to promote a digital economy
Play your Steam first-person shooters in full virtual reality with MyDream Swift
 As the launch dates of the Oculus Rift and the HTC Vive virtual reality headsets approach, so does the release of a ton of awesome VR gaming content. To gamers with full Steam libraries however, it’s kind of a shame that once they put the headset on, most of their favorite content is no longer available to enjoy. MyDream Swift is looking to bring old Steam content into the next… Read More
As the launch dates of the Oculus Rift and the HTC Vive virtual reality headsets approach, so does the release of a ton of awesome VR gaming content. To gamers with full Steam libraries however, it’s kind of a shame that once they put the headset on, most of their favorite content is no longer available to enjoy. MyDream Swift is looking to bring old Steam content into the next… Read MoreXbox Live now supports cross-platform multiplayer with PS4
 At this point, there's very little difference between the Xbox One and the PlayStation 4. But there was one key differentiating point. Xbox gamers could only play with Xbox and PC players as Microsoft was restricting access to the multiplayer component. Microsoft just announced that game developers can now create cross-platform multiplayer modes th Read More
At this point, there's very little difference between the Xbox One and the PlayStation 4. But there was one key differentiating point. Xbox gamers could only play with Xbox and PC players as Microsoft was restricting access to the multiplayer component. Microsoft just announced that game developers can now create cross-platform multiplayer modes th Read MoreSunday, 13 March 2016
Management overhead frustrates organisations' digital ambitions, says Capita study
Many UK business are in no position to roll out Windows 10 and are concerned about supporting diverse IT estates with their existing infrastructure
EMC adds DSSD D5 and VMAX all-flash arrays to enterprise portfolio
DSSD D5 brings array-based PCIe flash to market for EMC. VMAX hybrid arrays upgrade controller software to create two all-flash arrays, the 450F and 850F
Microsoft’s underwater datacentre: The pros and cons of running subsea facilities
Underwater datacentres can help providers save on land costs and cooling, but at what cost to the environment?
BCS calls for criminalisation of reckless data disclosure
The BCS believes criminalising reckless disclosure would reassure the public in how data is managed under planned surveillance laws
Remove Terraclicks.com pop-up (know the Manual Steps)
Terraclicks.com pop-up is actually a terrible adware infection that is stubborn, misguiding as well as nearly most of just about all extremely dangerous for exactly what you have to do in your PC. Additionally it is really a red flag for the System safety as well as for the actions that will user executes Online. These intrusive ads tend to be very stubborn along with hard to deal. Your webpage…


Saturday, 12 March 2016
Remove PCHealthWeb.com pop-ups instantly from your PC
Remove PCHealthWeb.com pop-ups, easy steps dealing the approach to uninstall PCHealthWeb.com pop-ups from computers safely That is quite important information for that complete PC users who devote their particular lots of energy more than your internet. PCHealthWeb.com pop-ups can be among probably your most terrible nasty redirect browser hijacker plan in which could capable to silently enters to the targeted…


Segment and segregate to defend data from cyber attack in 2016, urges F-Secure
Attackers will focus on critical data in 2016, mainly with the motive of cyber extortion, according to the latest threat report from F-Secure
Equinix taps into Open Compute Project to build open source datacentre ecosystem
Technology produced by Facebook-backed Open Compute Project gets snapped up by datacentre operator Equinix
Retailers not prioritising mobile are choosing to ignore their customers, says PayPal
PayPal’s director of mobile commerce warns retailers that mobile payments should be a top priority to provide the experience customers want
RSA 2016: Data compliance beyond the firewall
Vigitrust's Mathieu Gorge reports from the RSA 2016 conference, where a key discussion was storage and compliance in an age where data doesn't necessarily live in the firewall
How to remove iLotto Ads
Our safety expertsfound out that the iLotto Advertisements are usually caused…. How to remove iLotto Advertisements Exactly what is actually iLotto: Threat Classification: PUP/adware When your escalderon.com pc help online browser begins showing anyone lots ofunwanted web Ads through iLotto, our security analysis team strongly recommends youto runa malware system scan utilizing an up-to-date,reputable & reliable anti-malware softwarelike SpyHunter 4
Startup trials autonomous delivery robots in Greenwich
Estonian robotics startup Starship Technologies secures permission to trial self-driving delivery robots in Greenwich, south-east London
Indian suppliers are mopping up Nordic business
Indian IT suppliers are blazing a trail in the Nordic region with large deals and major local investments
Openreach to build FTTP networks for free on new housing estates
Openreach announces a major expansion of fibre broadband and will provide free FTTP networks to housing developments with more than 250 properties
Remove GameOn New Tab: Easy process to uninstall GameOn New Tab
Having all this, they dont even understand to fix this threat. Within these situations if Computer…. Not Too Long Ago many in the computer Customers had been reported with regards to GameOn New Tab that their Computers installed applications had been start doing function in irregular methods. Because well as, their own browsers were immediately randomly redirected in the direction of several unwanted and suspicious seeking websites
Friday, 11 March 2016
Remove Win32-mse-fixes.com pop-ups - Steps to uninstall Win32-mse-fixes.com pop-ups
It typically occurs inside the actual marked PC by means of obtaining attached using the third partys freeware plan files which are easily…. Remove Win32-mse-fixes.com pop-ups, Simple actions dealing how anyone can uninstall Win32-mse-fixes.com pop-ups coming from computers safely Win32-mse-fixes.com pop-ups is truly a Personal Computer browser hijacker infection which demonstrates its own existence infected PC through leading tons associated with malicious functions
451 Research warns of software-defined infrastructure skills gaps
Analyst house 451 Research warns CIOs against the dangers of failing to pair software-defined technology investment with staff training
The Christie speeds up SPC charts to improve clinical processes
Cancer specialist NHS trust implements statistical process control chart creation tool in data visualisation software Tableau to improve processes and save money
$1bn cyber bank heist thwarted by spelling error
Cyber thieves made 30 requests for the New York Federal Reserve to transfer nearly $1bn from the Bangladesh central bank’s account, but a typo and the volume of requests alerted banking officials
Payments regulator makes progress in introducing competition
UK payments regulator has slashed the time it takes for finance firms to join and use real-time payments system
PCIe SSD roundup 2016: Some stall while others progress
The PCIe SSD market is still important, but PCIE flash drive makers are split between those that continue to develop their products and those for whom product evolution has stalled
RTÉ leans on satellite broadband to cover Irish general election
Irish TV network RTÉ turned to satellite ISP Europasat to support its coverage of the country’s general election
Ofcom data breach highlights insider threat
That a former employee of communications regulator Ofcom stole data should act as a warning about the insider threat in every organisation, say experts
Technology and new finance firms will test banking industry
UK bankers now think fintech is a bigger issue than regulatory change, according to a study
Ex-Cabinet Office rep claims ‘simple’ tender rewrite could open up G-Cloud to Europe
Former Cabinet Office Crown representative says a simple rework of the G-Cloud tender could open up the procurement hub to public-sector buyers across the EU
Predictive maintenance brings efficiency to Trenitalia
New management system will help railway company reduce costs by applying predictive maintenance and data analytics to essential parts
Falling oil prices and disjointed data protection threaten Middle East datacentres
A fixation on datacentre ownership and mistrust of third-party services could impede enterprise IT in the Middle East
Remove Browseextended- Complete guide to eradicate
It will redirect to your site with out just about any concern. Posted in Browser Hijacker complete Threat Description: have your own System browser hijacks by your Browseextended that's why your are usually struggling to browse just about any websites as usual. Here can be a total help guide to eradicate effortlessly via PC:-


Third of knowledge workers expect their jobs to be computerised in five years
Knowledge workers realise their jobs will either change dramatically or disappear as the result of new technology, according to research
Innovate UK and UKTI lead Asean smart city mission
Smart city technology developers are heading to Malaysia and Singapore on a government-led trade mission
YouTube Gaming expands to new markets, improves its browsing and viewing experience on mobile
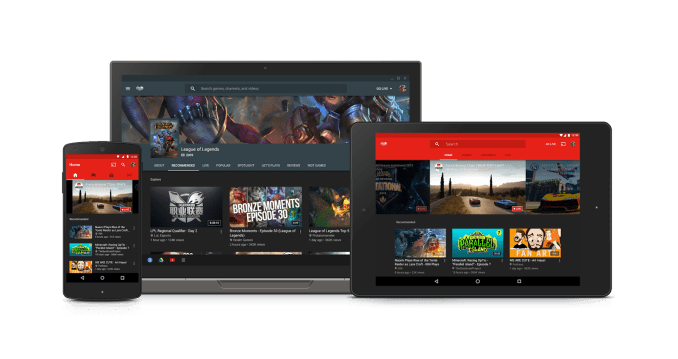 YouTube Gaming, the video network’s dedicated application for streaming and recorded game videos, and competitor to Amazon-owned Twitch, this morning announced an expansion into several more markets and a host of new features aimed at offering an improved browsing and viewing experience in its app. One of the changes will see the network more heavily promoting its “Live”… Read More
YouTube Gaming, the video network’s dedicated application for streaming and recorded game videos, and competitor to Amazon-owned Twitch, this morning announced an expansion into several more markets and a host of new features aimed at offering an improved browsing and viewing experience in its app. One of the changes will see the network more heavily promoting its “Live”… Read MoreUninstall Pcbooster.com ads from PC: Remove Pcbooster.com ads
In these scenarios if computer admins…. Since well as, their own browsers were automatically randomly redirected towards a few unwanted and suspicious seeking websites. Lately many with the computer users were reported regarding Pcbooster.com ads which their own Computers installed software had been begin doing function in irregular methods. Getting just about all this, that they dont even know to correct this threat
Thursday, 10 March 2016
IT outsourcing consultancy Alsbridge enters overlooked Australia
IT outsourcing consultancy sets up operations in Australia, which it says has been overlooked for outsourcing services
Challenger bank buys digital gaming specialist
Challenger bank Atom buys gaming expertise business Grasp to develop its online customer interfaces
Remove Browseextended- Complete guide to eradicate
Posted in Browser Hijacker Total Threat Description: Get your own System internet browser hijacks Through the particular Browseextended which is why your own tend to be not able to browse any web sites as usual. It will redirect to your site with out any concern. Here is truly a total guide to eradicate easily from PC:-


Mobile payments fund Tanzanian ambulance taxi service
NGOs in Tanzania use M-Pesa mobile payments to fund a life-saving ambulance taxi service in rural Tanzania
The problem with passwords: how to make it easier for employees to stay secure
An organisation’s IT security can be compromised if staff do not follow a strict policy of using strong passwords to access internal systems
RSAC16: Microsoft’s Windows PowerShell fully weaponised, security expert warns
Security expert Ed Skoudis says the PowerShell Empire open-source security tool is as much use to attackers as it is to defenders
Ransomware migrates to Apple Mac computers
Apple Mac users and security professionals must be more vigilant with the discovery of what is believed to be the first Mac OS X ransomware in the wild
Satellite data links to bring European air traffic management up to date
The European Space Agency awards Inmarsat a contract to develop a satellite-based data link communications system for air traffic management
DHL Asia-Pacific Innovation Centre incubates future logistics technology
DHL's innovation centre in Singapore is trying out the future logistics technologies it plans to introduce across its Asian business
Gartner warns IT leaders about the perils of using private platform as a service
Industry watcher Gartner warns IT leaders pursuing a private platform-as-a-service (PaaS) strategy to build cloud apps could be in for disappointment
Remove guardset.info: Uninstall guardset.info from PC
Recently many with the Pc Customers were reported about guardset.info which their own Computers installed programs were commence employed in irregular methods. Within these situations if Pc admins were…. While well as, their browsers were automatically randomly redirected towards a few unwanted and also suspicious seeking websites. having most this, these people dont even realize to fix this threat
Security Think Tank: Many breaches down to poor access controls
In the modern business environment, what are the most common access control mistakes – and how best are these corrected?
Broadband will reach 40% of Vietnam households by 2020, claims government
The Vietnamese government announces plans to increase access to broadband networks for its citizens, proposing a figure of 40% in four years
Virgin supplies Ethernet connectivity to Met Office supercomputer
The Met Office has awarded the contract to provide Ethernet connectivity for its next-generation supercomputer to Virgin Media Business
RWE chief executive points to SAP billing system as cause of npower losses
Npower has announced a radical restructuring plan, shedding 2,400 jobs on the back of losses of €137m. Its parent company’s CEO identified an SAP billing system as the source of the UK unit’s woes
Remove HELP_YOUR_FILES.PNG CryptoWall 4.0 - Easy to uninstall HELP_YOUR_FILES.PNG CryptoWall 4.0 from PC
Remove HELP_YOUR_FILES.PNG CryptoWall 4.0, easy actions dealing the means to uninstall HELP_YOUR_FILES.PNG CryptoWall 4.0 from computers safely Categorized straight into Ransomware family, HELP_YOUR_FILES.PNG CryptoWall 4.0 is extremely destructive as well as infectious computer threat which will come to the specific Personal Computer within the principal intention to be able to revenue funds form the PC admin. Whenever the PC internal files as well as program were…


Half of IT professionals struggle with enterprise patching
Many businesses struggle with the volume of software security updates and believe IT teams do not understand the difference between applying a patch and remediating a vulnerability, a survey has revealed
Lack of security knowledge limiting business initiatives, survey shows
Security concerns are limiting the adoption of cloud and mobility throughout organisations, according to the first Dell Data Security Survey
Stemettes raise awareness of International Women’s Day with weekend hackathon
Social organisation Stemettes ran a two-day hackathon to encourage girls into technology careers
Hilton hotel chain powers robot concierge with IBM Watson
The Hilton Worldwide hospitality channel is trialling a robot concierge named Connie, backed by IBM's cognitive computing programme Watson
Wednesday, 9 March 2016
CityFibre opens network to public sector supplier Updata
Urban fibre infrastructure supplier CityFibre signs a national agreement to allow Updata to offer services over its ultrafast network
BT CEO hints at change of direction on FTTP broadband
BT boss Gavin Patterson tells a conference he is working to enable Openreach to accelerate deployment of FTTP
Hyperscale computing boosts server revenue
The likes of Google, Facebook and Microsoft have bolstered server sales as they build increasingly powerful scale-out datacentres
How to Remove Extra-download-with-fast.com ads
Extra-download-with-fast.com ads is termed as an industrial notification that may request anyone to alter the default homepage in the browser in order to update software which it says will be completely out of date. This will ask anyone to click about certain link to have those needed updates even so it will just wind up in the installation…


Ways to Remove Intabsearch.com Redirect
But actually it is actually a type of browser hijacker programs that can configure itself to start out instantly whenever you commence the random web browser. Intabsearch.com will be not truly a virus. In Which would end up being to say, this browser escalderon.com pc help hijacker can be able to replacing your existing homepage on your own browser and also causing endless redirection. Besides, you can encounter a…


Remove Searchandstreamtv.com: Simple steps to delete Searchandstreamtv.com from your PC
Searchandstreamtv.com is actually browser hijacker infection that is created to alter browser settings. That is actually advertised like a helpful tool that may help Pc customers in order to easily use of on-line TV. However, it is an irksome websites in which carry your current PC…. So, your research queries always obtain redirected in order to sites that an individual pchelp escalderon.com simply had no intention of visiting
Tuesday, 8 March 2016
How to Get Rid of Virusdefense.info Pop-up
Virusdefense.info is actually considered as the possible ad-supported platform which will display fake messages and data for you to fool pc users. This particular say will state that your product is dangerous. Next, you…. A Person needs to be careful in the big event you get redirected to be able to this scam web site accidentally. The Actual goal of this website would end up being to cause panic and also cause a person to anxious
Detect and uninstall Flexible Family Ads - Remove Flexible Family Ads
If yes, then scanning this post will escalderon.com pc help effortlessly supply all involving you information based on experts recommendations..!!!. The Windows system may well being the difficult cake to swallow credited to unfortunate existence regarding flexible Family Members Advertisements inside it in which made anyone search effective methods to resolve such issues
Sunday, 6 March 2016
Legal spears fly at Privacy Shield
Police Scotland is investigating the implications of the end of Safe Harbour. Service providers must comply with UK law, regardless of where they are based
Combine data mining and simulation to maximise process improvement
Data mining and computer simulation can be used together to better model and improve industrial processes, city development and other complex systems
UK insurance industry prioritises big data in 2016
The UK insurance industry is making a priority of big data to make more personalised customer offers in 2016, research from Teradata reveals
Businesses covering up cyber attacks, says IoD
The Institute of Directors warns that businesses are actively covering up when they have been the victim of a cyber attack
CSA outlines CIOs’ top 12 cloud security concerns
Cloud Security Alliance’s research team uncovers the “dirty dozen” off-premise threats
RSAC16: Security industry needs to do more, says Intel Security Group head
Chris Young calls on security industry to pay more attention to cyber threat intelligence sharing and encouraging people to become information security professionals
European Commission releases legal details of EU-US Privacy Shield
EC claims the publication of legal texts and written assurances marks the start of the new-look data-sharing agreement coming into force
Saturday, 5 March 2016
Striving for a balanced mobile world: the Connected Women of MWC
At Mobile World Congress in Barcelona, the GSMA’s Connected Women initiative began a new drive to connect more women in the developing world. Computer Weekly meets programme director Claire Sibthorpe
Bet365 donates Erlang libraries to GitHub
The open-source initiative will help to drive adoption of the Erlang functional programming language among enterprise developers
Miserden has most miserly broadband speed, report claims
Speed tests carried out by Cable.co.uk have located the slowest average broadband speeds in the UK, in the village of Miserden in Gloucestershire
'Complacent' Home Office failed to take responsibility for e-Borders problems
The Public Accounts Committee (PAC) criticises the Home Office for allowing the e-Borders programme to run eight years late and £500m over budget
Australia’s corporate giants recruit digitally-minded outsiders to drive transformation
Big Australian businesses are turning to digital professionals from outside rather than promoting from within
BBC reporter demonstrates mobile phone hack to steal from producer's bank account
A reporter on the BBC Radio Four You and Yours programme has managed to hack a NatWest online bank account and extract cash
MasterCard named as VocaLink suitor
MasterCard is reportedly in talks with the banks that own payments provider VocaLink over a £1bn takeover
Facebook to overhaul UK corporation tax-paying regime – report
Social networking giant plans to book larger deals with British firms via its UK arm, paving the way for it to pay more corporation tax
Reinstating Moore’s Law: a next-generation transistor for mobile technology
Research into a new generation of transistors could end a decade of stagnation in computing speed and deliver a step-change in processing power, says the National Physical Laboratory’s Mark Stewart
Meg Whitman uses Q1 results to argue the case against Dell/EMC
HPE posts its first financial results following the split of the business
Link from “The Legend of Zelda” pops up on Google Maps today
 Google has hidden a little surprise today in Google Maps for fans of “The Legend of Zelda” – the company is celebrating the release of the new game, “The Legend of Zelda: Twilight Princess HD” for Wii U by turning Google Maps’ Pegman figure into the game’s hero, Link, for the next five days. You’ll find the Link avatar in the same spot as you… Read More
Google has hidden a little surprise today in Google Maps for fans of “The Legend of Zelda” – the company is celebrating the release of the new game, “The Legend of Zelda: Twilight Princess HD” for Wii U by turning Google Maps’ Pegman figure into the game’s hero, Link, for the next five days. You’ll find the Link avatar in the same spot as you… Read MoreFriday, 4 March 2016
Security Think Tank: Access control is key to protecting against cyber attacks
In the modern business environment, what are the most common access control mistakes and how can these best be corrected?
RSAC16: Cyber criminals are hiding in plain sight, says RSA report
Cyber criminals are using social media as a communication and sales channel, not just for reconnaissance and phishing, an RSA study has revealed
Virtualisation and the cloud aid disaster recovery in Spain
As virtualisation and cloud services take hold, Spanish organisations can take advantage of less costly and more flexible responses to the threat of unplanned outages
Equinix and Interxion set out 2016 global datacentre expansion plans
Colocation rivals outline their investment intentions and priorities for the year ahead
MasterCard uses artificial intelligence to help UK sales team
Financial services firm is deploying AI software created by one of the IT startups it supports in a global programme
World’s biggest banks complete joint blockchain trials
Forty major global banks have jointly run tests of the use of blockchain in wholesale banking
RSAC16: UK government to change tack on cyber security
The UK government is thinking about becoming more interventionist to ensure the next five years yield a better return on investment in cyber security, according to CESG cyber security head
US researchers begin solar-powered datacentre research project
Massachusetts-based project aims to uncover how best to integrate datacentres and smart grids
Civil engineering firm goes follow-the-sun with Azure cloud and Talon
Robert Bird deploys Talon Storage CloudFAST with Microsoft Azure cloud storage on the back end to enable 24-hour working between offices on three continents
Ministry of Justice chases IT department whistleblower for tribunal costs
The Ministry of Justice (MOJ) is claiming costs from a system analyst who brought an employment tribunal raising allegations of bullying at the Legal Aid Agency
Thursday, 3 March 2016
Security Think Tank: Top five access control mistakes
In the modern business environment, what are the most common access control mistakes and what is the best way to correct them?
Ofcom badly wrong on Openreach separation, MPs told
The decision not to separate BT and Openreach has not solved any regulatory issues and will not address the problems at the heart of broadband roll-out, a Select Committee hears
IoT adoption held back by lack of business case, software and skills
The internet of things is at the top of Gartner’s Hype Cycle, but many organisations cannot build a business case to invest in IoT projects
Telecoms firms launch Stem mentoring scheme for girls
BT joins Ericsson, O2 and Vodafone to create a mentoring scheme encouraging girls into science, technology, engineering and maths (Stem) careers
Security Think Tank: Policies and procedures vital for successful access control
In the modern business environment, what are the most common access control mistakes and what is the best way to correct them?
Finland’s Kone chooses IBM for IoT push
Lift manufacturer is using IBM Watson as part of its internet of things strategy after a multi-year agreement with the IT giant
Virtualisation rolls on, but still less than 50% of workloads are virtualised
Survey finds server virtualisation is top way to upgrade datacentres, while public and private cloud storage gains serious momentum
Virtual insanity: Is 2016 the year users go big on VR?
At Mobile World Congress 2016 in Barcelona, virtual reality appeared to emerge as a technology that is at long last hot to trot – but is it still a lot of virtual hype?
RSAC16: Microsoft’s chief legal officer Brad Smith champions encryption
Information security requires a comprehensive approach including strong encryption, says Microsoft chief legal officer Brad Smith
Swedish outdoor powertool maker outsources to HCL
Husqvarna has expanded an existing IT outsourcing agreement with Indian IT services firm
Drown attack sinks SSL security
Researchers publish paper outlining how an attacker could crack the TLS security protocol to gain access to millions of secure websites
AWS cuts cloud data transfer fees for academic and research user groups
Cloud services giant Amazon Web Services (AWS) rolls out discounts in bid to lower the cost barrier to making scientific discoveries
Lifting of Iran sanctions brings hope to regional IT industry
Nuclear deal could mean new era for IT suppliers, distributors and channel partners in the Middle East, but caution is urged
RSAC16: RSA’s Amit Yoran comes out in support of strong encryption
A policy of weakened encryption would harm US economic interests and undermine those trying to defend digital environments, according to RSA president Amit Yoran
HTC claims 15,000 pre-orders in 10 minutes for its Vive VR headset
 A possible tidbit of early sales data for one of 2016’s flagship virtual reality systems: the HTC-Valve Vive has apparently racked up more than 15,000 pre-orders in less than 10 minutes, according to a tweet by HTC VR dev Shen Ye. Read More
A possible tidbit of early sales data for one of 2016’s flagship virtual reality systems: the HTC-Valve Vive has apparently racked up more than 15,000 pre-orders in less than 10 minutes, according to a tweet by HTC VR dev Shen Ye. Read MoreWednesday, 2 March 2016
RSAC16: US works on data access agreement with UK
The US is negotiating with the UK to establish a new framework that will permit UK authorities to access electronic communications directly from US companies
Legacy systems stand in the way of customisation for banks
Banks are hindered by legacy systems that prevent them from delivering a personalised customer experience
Datacentre heat reuse: Why aren’t more operators doing it?
With the datacentre industry’s sustainability habits coming under increasingly close scrutiny, we find out why operators are not rushing to reuse their waste heat
Buckinghamshire Council frees transport data to create smart suburbs
Local authority has partnered with IoT platform developer InterDigital to establish a county-wide smart transport model
Record UK cash withdrawals, but is it just a stay of execution?
The amount of cash withdrawn from UK ATMs last year was up on the previous year despite the arrival of technology-enabled alternatives
Cern uses AppDynamics to improve application performance
The home of the Large Hadron Collider has deployed AppDynamics’ APM tool to improve the speed and efficiency of application monitoring
Australia’s fintech community will target China
The Australian government is injecting money into the country’s financial technology community to help firms break into lucrative Asian markets
RSAC16: Cyber attackers still after low-hanging fruit, dark web study shows
Tracking a cyber adversary that is recruiting and the skills they desire can improve the overall maturity of an organisation’s security programme, according to Digital Shadows
Cyber security professionals in Singapore could get 20% pay rise
E-commerce and cyber security professionals in Singapore could gain 10 to 20% pay rises if they move companies, due to increased demand of niche IT skills
Strange sensations: HTC’s brave new virtual world
 The first thing I notice is a feeling of weight on my face. Followed by a sensation of standing in boundless space. A monochrome 360-degree vanishing point vista winks into view. I look around, blinking into the far distance and very quickly my adjusting eyes fill with grit… Welcome to the weird world of 21st century virtual reality. Read More
The first thing I notice is a feeling of weight on my face. Followed by a sensation of standing in boundless space. A monochrome 360-degree vanishing point vista winks into view. I look around, blinking into the far distance and very quickly my adjusting eyes fill with grit… Welcome to the weird world of 21st century virtual reality. Read MoreTuesday, 1 March 2016
New York judge blocks FBI iPhone warrant
Judge rules that Apple does not have to help the FBI unlock the iPhone of a suspected drug trafficker
Data sovereignty issues drive up cost of cloud for European CIOs
Addressing data sovereignty concerns means European CIOs are forced to pay more for cloud services than their US counterparts
Security Think Tank: Password management tops list of access control issues
In the modern business environment, what are the most common access control mistakes and how best are these corrected?
DDoS attack threat cannot be ignored
Criminal activity has become the top motivation for distributed denial of service attacks as the average attack become strong enough to down most businesses – so taking no action is not an option
CIO interview: Anders Candell, Stora Enso
CIO at Finnish pulp and paper manufacturer shares advice for shouldering a new CIO position and guiding the business towards innovative technology
The business processes behind services management
We take a look at the essential steps an organisation must take to multi-source or bring in-house IT services
Mobile Infrastructure Project was a failure, admits Vaizey
At a Westminster Hall debate, digital economy minister Ed Vaizey conceded the £150m Mobile Infrastructure Project to address "not-spots" was largely unsuccessful
Global finance regulator to examine fintech risks
Global financial system stability group FSB will take a closer look at financial technology companies
Subscribe to:
Comments (Atom)